A Forbes article claimed Xiaomi smartphones are collecting browser data including from incognito sessions and sending to servers in Russia and Singapore. While rampant data collection is indeed an unfortunate status quo of internet companies, it’s the nature of encoding that Xiaomi is using that has alarmed cybersecurity experts. Xiaomi took out a detailed blog explaining their privacy policies and data collection practices with Manu Kumar Jain even recording a video to debunk the ghastly claims made by the Forbes article
While the response is listed out in full detail on Xiaomi’s blog, it can all seem a litte too technical. To help you understand, we have broken each claim made on the Forbes piece and Xiaomi’s response to it —
Claim 1: Mi Browser and Mint Browser tracking all activity, even when in incognito
Gabriel Cirlig, the cybersecurity expert quoted in the Forbes piece was the first to discover this. He found the Mi browser (installed by default in all Xiaomi phones) as well as Mint Browser (available on Google Play Store with thousands of installs) were tracking the URLs you visited as well as the search terms you used on DuckDuckGo as well as Google Search. The browser tracked the URL even when you are in the private or incognito mode. This data is being sent to servers owned by Alibaba in Russia and Singapore, and rented by Xiaomi.
Xiaomi’s response
Xiaomi admits to collecting data such as system information, preferences, user interface feature usage, responsiveness, performance, memory usage, and crash reports. These are anonymised and aggregrated and cannot be used to identify an individual. Xiaomi also admits that URLs are collected to identify slow-loading web-pages but doesn’t mention whether it also looks at what the user is searching on search engine websites. Furthermore, Xiaomi states the data collection is done with user consent which the user permits when they agree to the terms and conditions when setting up a Xiaomi smartphone.
The company further confirmed that it collects usage stats while in incognito mode as well, and usage stats also includes URLs which is ironic considering the incognito mode is enabled so that such data is not collected.
Counter Response from cybersecurity researchers
So, Xiaiomi have published a blog, which I think aims to refute what myself, @hookgab and @iblametom are presenting.https://t.co/b8YH1pa2xo Let's tear it down.
— Cybergibbons (@cybergibbons) May 1, 2020
Another cybersecurity expect who Forbes spoke to, Andrew Tierney (goes by the alias @Cybergibbons) tweeted out a proof of concept which countered Xiaomi’s response. While most of it is too technical to explain in simple terms, the video basically shows that the data collected has a UUID or a universally unique identifier which easily lets someone identify where the data came from.
Claim 2: Sending data to remote servers using sub-standard encoding
The researchers also claimed Xiaomi is storing the data in foreign servers based on Russia and Singapore. These servers are owned by Alibaba and rented by Xiaomi. They have web domains registered in Beijing. Furthermore, it was found Xiaomi is using base64 encoding which the researchers claimed can be easily decoded on the client-side, once again potentially revealing individual identities.
Xiaomi’s response
“Xiaomi hosts information on a public cloud infrastructure that is common and well known in the industry. All information from our overseas services and users is stored on servers in various overseas markets where local user privacy protection laws and regulations are strictly followed and with which we fully comply.”
Indeed, this is a standard practice among many software companies. Collecting aggregated and anonymised data is performed by the largest internet giants like Google and Facebook. And this is one place where Xiaomi alone can’t be taken to task.
Xiaomi also claimed the data sent to overseas servers are all anonymised and there’s no way it can be traced back to an individual. However, the researchers found Xiaomi is using base64 encoding which is easily trackable, at least from the client side.
Xiaomi’s response didn’t really touch this part of the claim. It did however state that they use TLS 1.2 encryption standard. As a result, while it may be difficult to intercept the data in transit, there’s no way to tell how the data is treated once it reaches it destination.
Claim 3: User data collected isn’t anonymous, as claimed by Xiaomi. The UUID is specific for each user for 24 hours and not randomly assigned as suggested by Xiaomi
Gabi and other researchers found that the data shared from the Mi Browser and Mint Browser all carry unique identifiers which are specific for individual devices. For instance, two sets of data sent from the same smartphone within 24 hours. will carry the same UUID, which again potentially allows server clients to identify the origin of the data.
Xiaomi’s response:
“This screenshot shows the code for how we create randomly generated unique tokens to append to aggregate usage statistics, and these tokens do not correspond to any individuals.”
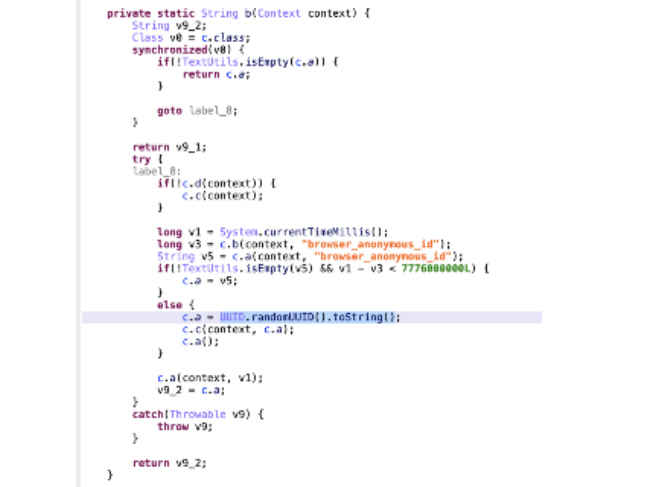
Counter response by the researchers:
The POC video released by Andrew clearly shows that the UUID is the same for data sent within 24 hours, debunking Xiaomi’s claim of using randomised tokens. He even debunked the screenshot shared by Xiaomi on Twitter.
They present this as evidence that they "create randomly generated unique tokens" that "do not correspond to any individuals". This code shows nothing of the sort. pic.twitter.com/B4mkhU7ZKH
— Cybergibbons (@cybergibbons) May 1, 2020
Is it fair for Xiaomi to collect private browser data?
Xiaomi took a day to jot down its side of the story which maintained that the research done by Forbes for the story is flawed. The company further stated that collecting usage data is a standard industry practice. Almost every web browser in the world collects user data. However, it’s the nature of collecting data by Xiaomi that is under scrutiny.
For instance, while Chrome and Firefox are known to keep track of the URLs you visit, collecting data generate during an incognito sessions isn’t heard of, and can’t be considered normal or an industry practice which can be accepted.
The private mode exists specifically to prevent URLs being listed on browser history and to prevent cookies and other trackers to be inserted. Including search terms is even more alarming.
Furthermore, which it’s proven that the data stays encrypted while in transit, having an UUID means the data can potentially be traced back to the individual.
Xiaomi’s response of calling out the research as flawed without substantiating the claim with relevant evidence and pointers isn’t right. The company needs to come clean of its data collection practices in light of the recent revelations.
UPDATE: Xiaomi updates Mi Browser and Mint Browser to include opt out of incognito browser data collection
Xiaomi issued an update on May 4 for Mi Browser, Mi Browser Pro and Mint Browser apps on Google Play Store for all users. The update includes an option to switch on/off aggregted data collection in incognito mode.
from Latest Technology News https://ift.tt/2zagzEU


No comments:
Post a Comment